Table of Contents
What is OAuth?
OAuth Authentication in OIC is used when applications want to programmatically invoke integrations without any user intervention. The OIC process needs to be oAuth authentication Enabled.
The client application impersonates the user by sending the user assertion to Oracle Identity Cloud Service while requesting token access. An access token is returned in the user context.
The user can either represent a human or a service integration account created for identifying a specific calling application.
OAuth authentication is used when an IDCS user is to access or trigger an OIC process.
There are two common approaches to test. a 3 Legged Flow and A two-legged flow.
Let’s see the three-legged flow which can be used to test A oAuth Process from the postman. This requires mannual interventions. While two legged can be directly called by calling application without any user intervention.
Steps to implement OAuth Authentication in OIC
- Create a Sample Hello world OIC process which returns a message ‘e.g Success’
2. Make sure to use the rest connection authentication as OAuth in the process in step 1.
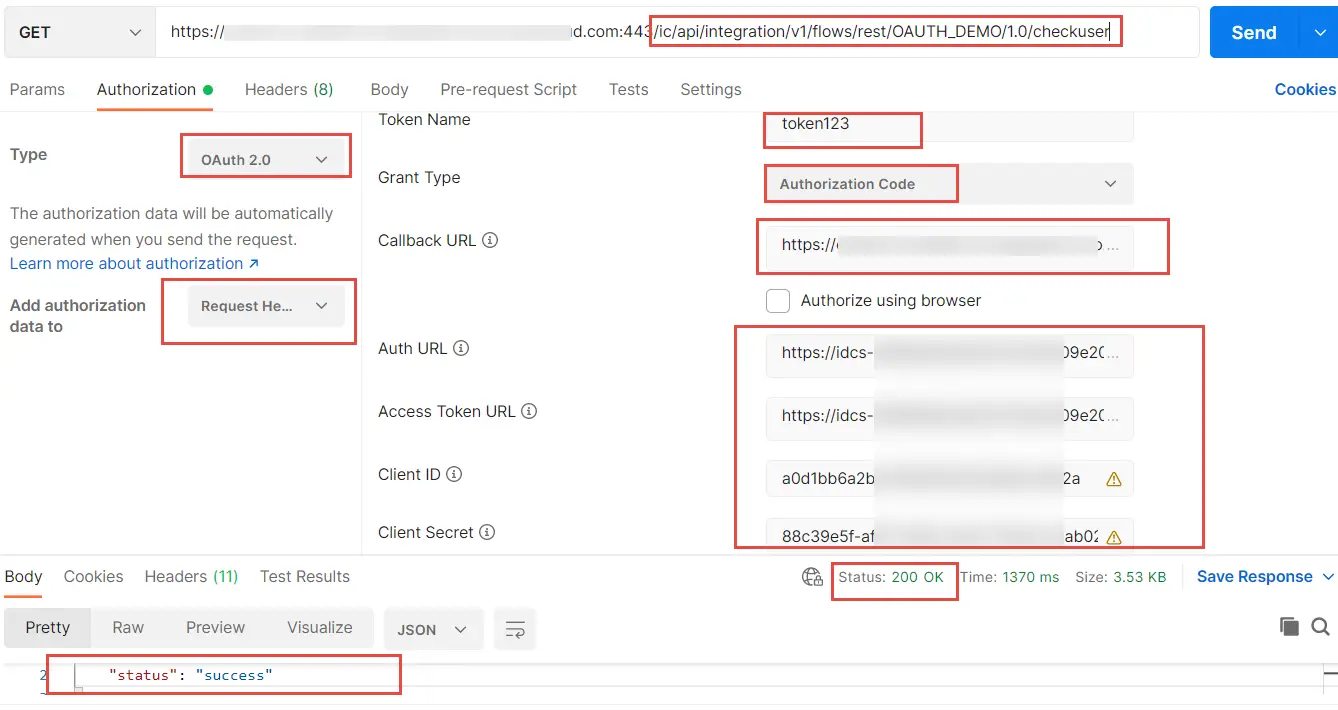
3. Use postman and put request URL as your oic process endpoint URL.
E.g https://(yourdomain.com):443/ic/api/integration/v1/flows/rest/OAUTH_DEMO/1.0/checkuser

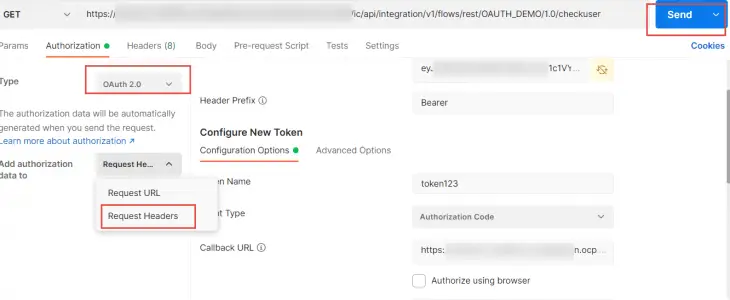
4. Select Autorization Type as OAuth.
5. Select Grant Type as “Authorization Code” from the list of values
6. Callback URL is the Redirect URL provided in the IDCS Application configuration . This url is what you get as callback when you register your oic application in IDCS
(e.g. https://yourdomain.com/icsapis/agent/oauth/callback)
7. Auth URL is the IDCS instance URL with /oauth2/v1/authorize appended to it .this is the login url domain you get when you login to Oracle OIC. (e.g. https://idcs-xxxx.identity.oraclecloud.com/oauth2/v1/authorize)
(e.g. https://idcs-xxxx.identity.oraclecloud.com/oauth2/v1/authorize)
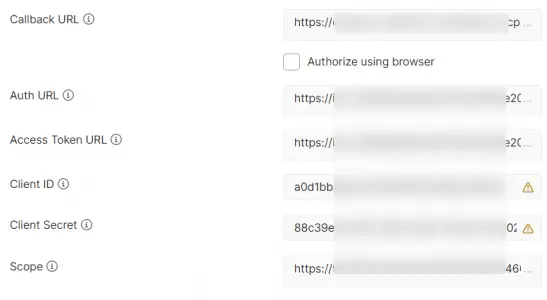
8. Access Token URL is the IDCS instance URL with /oauth2/v1/token appended to it
(e.g. https://idcs-xxxx.identity.oraclecloud.com/oauth2/v1/token)
9. Client ID is from the General Information section of the IDCS Application configuration. You will get this from your IDCS screen. Ask your IDCS Administrator.
10. Client Secret is from the General Information section of the IDCS Application configuration. Ask your IDCS Administrator
11. Scope is from the Client Configuration section of the IDCS Application configuration
(e.g. https://yourdomain.com:443urn:opc:resource:consumer::all)
Other fields can be left as default
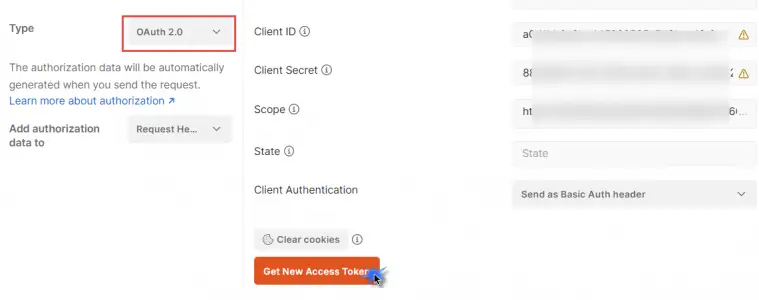
11. Once all the above values has been entered in the postman ui fields hit GET NEW ACCESS TOKEN button , click on Request Token to retrieve the OAuth token from IDCS for use in the OIC integration trigger:
12. The process for getting the token requires you to authenticate with IDCS, so a popup window will be presented with the IDCS login screen:
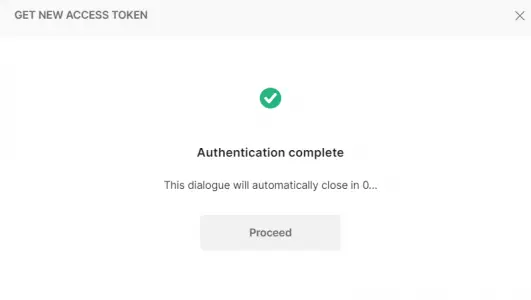
13. Once you authorize yourself with IDCS, Postman will present the JWT Access Token provided by IDCS.
14. In the MANAGE ACCESS TOKENS dialog that returned the new access token, select Use Token button.
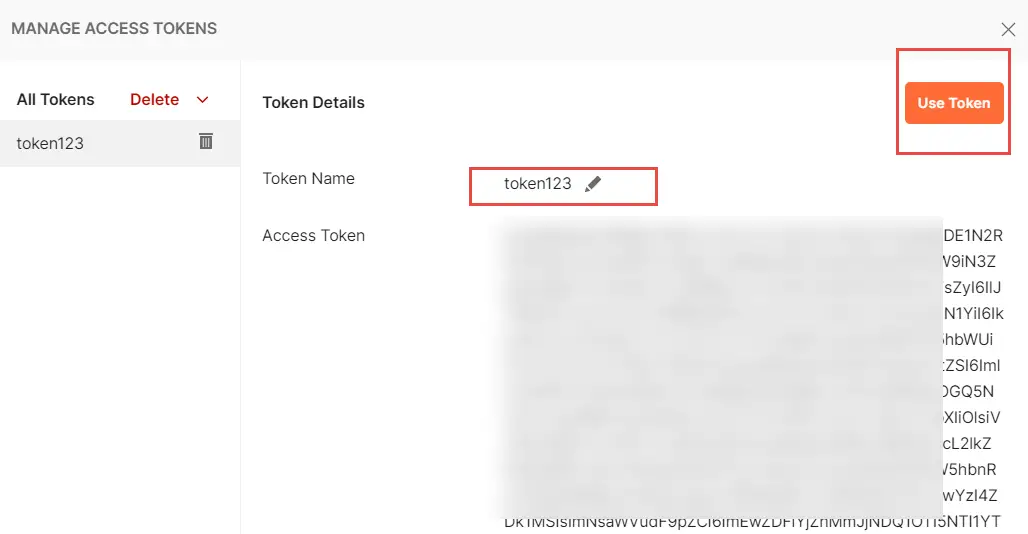
15. At this point we have all the required information to trigger the OIC integration using OAuth. In Postman, click on the Preview Request button to populate the Bearer Header in the request:
16. In the authorizaton tab, select Add authorization data to Request headers .You can see this header by switching to the Headers section of Postman.
Once you see the header present ,You can hit the “Send” button and the OIC process should trigger.
{
"status": "success"
}Assuming we did all the correct configurations, you will see the results in Postman under the Body section (where you can see the request/response messages) as per the images above.
You can see the executed process in the OIC monitoring Screen.
This completes the 3 legged demo using postman.
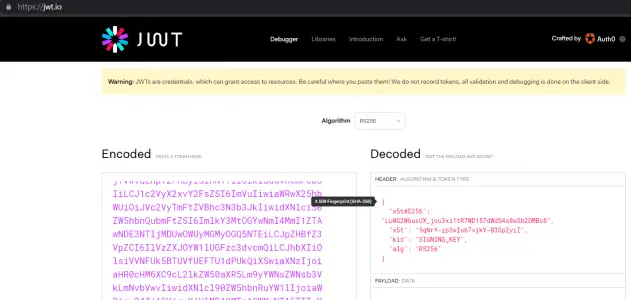
To understand more about the JWT token generated
go to jwt.io and put the token in the encoded field . you will see the decoded data on the right side which show what this token is about.
To know OAuth in Detail
[content-egg module=Udemy template=list]
FAQs:
When to use Oauth in OIC?
When you want to call your oic process with single sign on and do not want to use the local OIC user.
Any roles to be required by the user?
The OIC Service Developer / Invoker should be added to the calling user role. Also the user should have access to call the deployed Application in IDCS.
Is there a time limit for the token?
Yes the token has a expiry time and it has to be used within the period . This is defined in IDCS.