With SaaS applications becoming the preferred choice for many customers, SaaS Security Best Practices aligned to industry standards should be followed by vendors when they design their SaaS services.
Any business signing up with a cloud vendor should be confident of giving custody of their data to the vendor. The confidence comes when the vendor follows the latest cloud computing standards and has required certifications or has proper risk-mitigating controls.
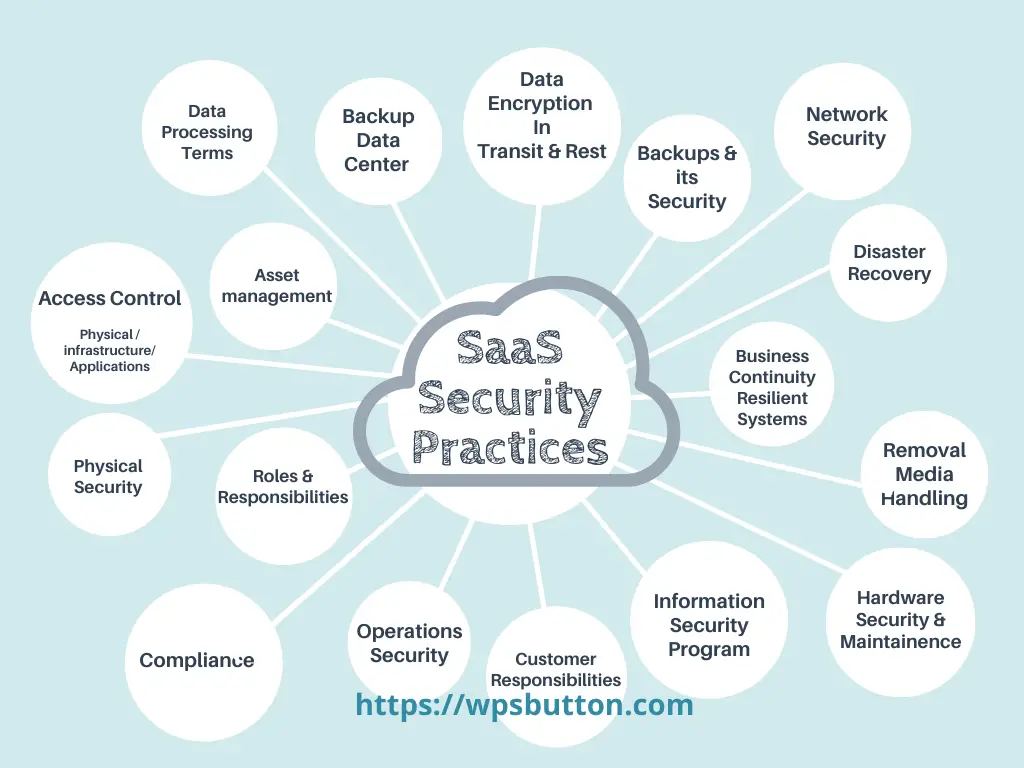
For implementing SaaS security best practices by an organization there are many areas that should be covered.
Let’s see the important ones one by one.
Table of Contents
Factors affecting SaaS Security Best Practices
There are several security areas to be addressed as part of overall cloud security . Lets see them
Cloud Computing Information Security Practices
When a company is providing SaaS services it should follow standards of cloud information security laid down by some of the security organizations like CSA, NIST. it should have a data processing agreement with each customer as per their needs and its policy which should be captured in the ordering document.
There standards cover area of data handling , firewall , internal security , network security , access controls and more.
The policies should align and complement the internal organizations information security practices.
Asset Management Policies
A company should have a well-defined asset classification and management policy in place. This should include the inventory of assets recorded and the ownership history records.
The responsibility of the asset owner should be defined as well.
There should be policies to bring a new asset or retire an asset from the cloud infrastructure. It should also govern the handling and maintenance of assets during its lifecycle.
Access Control
Access control is one of the major areas in the information security context where the saas security best practices define many controls put in place, like :
Physical Access Control
All equipment’s and systems at the data center should be physically secured and access to employees and workers should be provided on need to know basis and by default it should be denied.
All personnel’s accessing or visiting datacenter should have proper identification badge and a policy should be in place so that there is no unauthorized entry.
Logical Access Controls
Logical access controls applies to areas of cloud computing infrastructure and services like
- Administrative access to servers: Who can access admin systems inside the vendor’s organization.
- Role-based access controls: Every user should have roles and privileges based on their job role.
- User access management: Customer’s user access should be governed by its policy.
- Passwords Policy and complexity: Strong password policy should be implemented.
- Session Management and Timeouts: Session lockouts and a unique sign-in policy should be there.
- Privilege management: Privileges should be periodically reviewed when employees change job roles or get terminated.
- Network access controls: Security controls to allow only authorized traffic should be there
- System Access controls: Strong authorization and authentication controls should be there.
- Data access controls: Role-based access controls should be there for data-level access.
- Support and Operations Controls: any support staff should have need-to-know basis access.
- Employee Access controls: Every employee access should be provisioned via authorization.
- Access Review Policy: All accesses of employees and contractors should be reviewed periodically.
Cryptography
Cryptography is the security mechanism where the information is encrypted using standard encryption algorithms. The encryption algorithms may be 128 bits or more. The more is better in terms of security.
The cryptography applies at different levels
Data in Transit
At the network level encryption algorithms are applied to all the data with is transmitted over the network. The SaaS service when access by an internet browser should be secured with HTTPS protocol. The services should have browser certifications for better security.
Data at Rest
Encryption algorithms are applied to all the data at rest like in tables and file systems.
Media Encryption
All media used for storing data and information should be encrypted. This includes both fixed and removable media devices like thumb drives and tapes.
Encryption Key Manager
A good SaaS security practice is to have a dedicated computing system to manage the keys with which data is encrypted. There may be different keys for different kinds of data sets.
Also, the Keys need to keep changing for security purposes, so a policy should exist to keep changing/rotating the keys.
Key Administration
Role-based access control should be strictly implemented when assigning privileges to users for managing keys.
Physical Security
Procedures should be in place to secure all physical assets of the SaaS cloud infrastructure. This may include manning the data center with security guards 24x7x365, Fencing with high walls, Identification badges for all entrants, CCTV monitoring and alarms, Biometric access controls.
The Infrastructure equipment should be kept under a controlled environment with HVAC (Heating, ventilation, and air conditioning ) setups. Detection systems for an environment like heat, dust, fire smoke, vibrations should be installed.
The locations of installations of systems and other equipment’s should be carefully planned. Underground cables should have proper markings and should avoid public routes.
Communications Security
The communication security consists of
Network Security Policies
A SaaS services vendor should have policies defined to access network for scanning and testing and should be able to detect any unauthorized scanning . All Scans and Vulnerability testing should be done by authorization.
Transport layer security should be as per standards
In case Wireless networks are used strict standards should be maintained.
Network Segregation
Networks should be segragated based on traffic , security and availability.
SaaS companies can have different segregated networks for
- Internal
- External
- VPN
- Business Reporting
- Operating systems
Access control Lists (ACLs) should be implemented at Router, Switches, Firewall and Load Balancer levels to ward of DOS and DDOS attacks.
Network Intrusion Detection System
Intrusion Detections should be implemented at the network level to ward of Intrusions to networks. Possible options can be for protection and detection. They should be able to detect suspicious activities.
SaaS Running Operations Security
Once the SaaS service is provisioned and access is granted to customer for use the operations should have the security controls
Services offered
Controls should be there to provide only the ordered SaaS products. As SaaS services are on a shared tenancy model so this becomes very important.
Change Management
The SaaS software may need periodic updates for adding new features, patching for bugs, etc. This change management is generally done using different instances for development, test, and production. There should be proper security controls when provisioning access to dev and test instances and the production data on test instances.
Standard Change management policy with controls should be implemented.
Capacity Management
Capacity or the Load on the SaaS services should be decided based on the order from a customer and proper sizing of resources should be done. All the resource capacity and utilization should be monitored continuously to track any abnormal activity for e.g CPU utilization, storage, network bandwidth, etc.
Malicious Code protection
The SaaS Software should undergo secure coding practices for defense in depth against malicious codes.
Test plans for static and dynamic analysis should be implemented before every patch release.
This may include penetration testing of the SaaS services by third parties for network and applications.
Backups
Taking regular backups is essential in the SaaS services model. Both online and offline backups should be done and the application state should be also backed up. Devices used for backup should be secure and encrypted.
Physical Media handling , Transit and Disposal
All physical media handling , transfer and disposal should be done in accordance with Standards as this is another area which may not get attention.
Logging & Monitoring
All data, transaction activities should be logged 24x7x365 days at the application, network, and database-level to track issues to remediation.
Systems & Server Maintenance
Policies should be in place to have the hardware components serviced at regular intervals and if components are reaching end of life they should be securely disposed. Any patches upgrades should be made available and applied thorough proper change management procedures.
Incident Management
There should be a program for incident management and reporting where suspicious incidents are identified and remedial actions taken.
This may require to study logs from different systems at real time and alert to the respective team handling the remedial steps.
Third Parties
Third parties involved should be minimized as much as possible. In case a third party is used to provide a section of service there should be a proper service agreement and should have controls as per standards in the area they are serving.
Business continuity and Disaster Recovery BC/DR
All SaaS services should be modelled with best possible business continuity and disaster recovery policies so that the downtime of a services is minimum and data loss can be minimized. Also Recovery to a certain point should be made possible as per standards.
Resilient Systems
The infrastructure should be resilient to provide high availability and recover transactions in case of disaster. The RTO – Recovery time objective and RPO – Recovery point objective should be as per cloud computing standards.
Disaster Recovery
There should be a disaster recovery plan which can detect and call out a disaster to determine the damage and start the restoration of primary data center services.
The plan should cover activities for assigned resources during the interruptions and strategy for recovery.
All the DR Plans should be Table tested so that when the real disaster happens most of the activities are covered.
Customer Responsibilities
Finally there should be some responsibility with the customer as well when using SaaS services, Such as what data they store and in what form. Proper agreements should be in place regarding access of Personal or customer confidential data and its usage.
A SaaS vendor may not be aware of the criticality of some of the data and if required they should be made aware by the customer for any extra security measure like masking , sharing or testing usages.
In Short Customer should be fully aware of the risks of using a cloud computing SaaS Service. Understanding the risks and benefits will help in taking better decisions on using SaaS services for certain business processes.
So these were some of the points and can be considered as a framework for building a SaaS security checklist.
Thanks for reading, do let me know your comments.